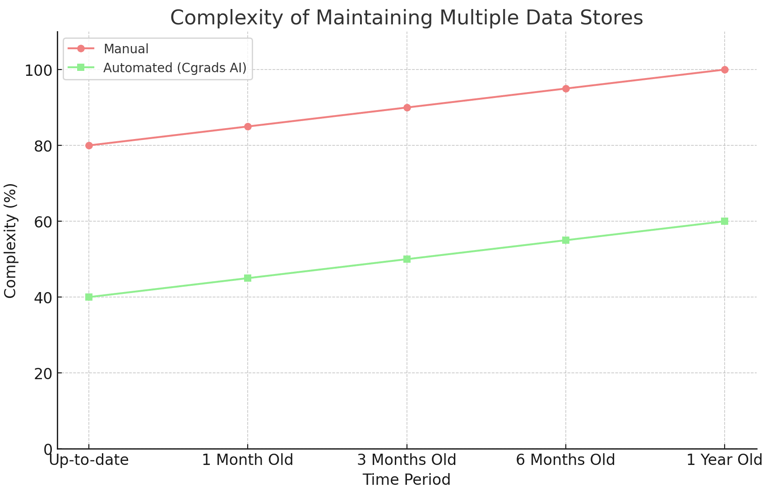
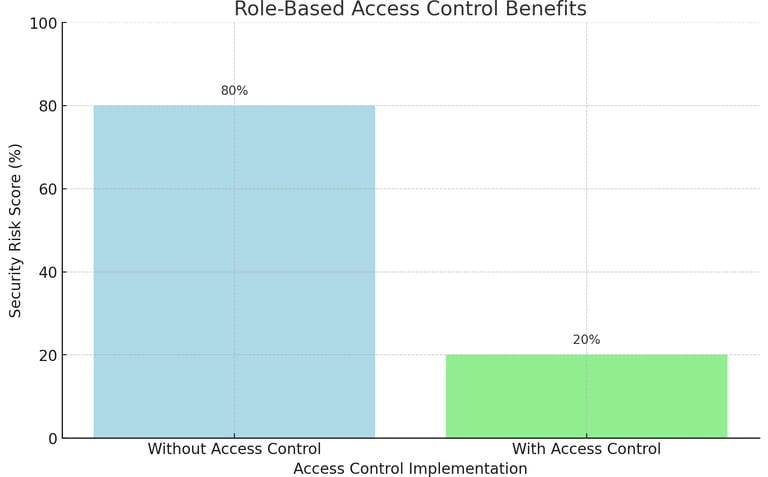
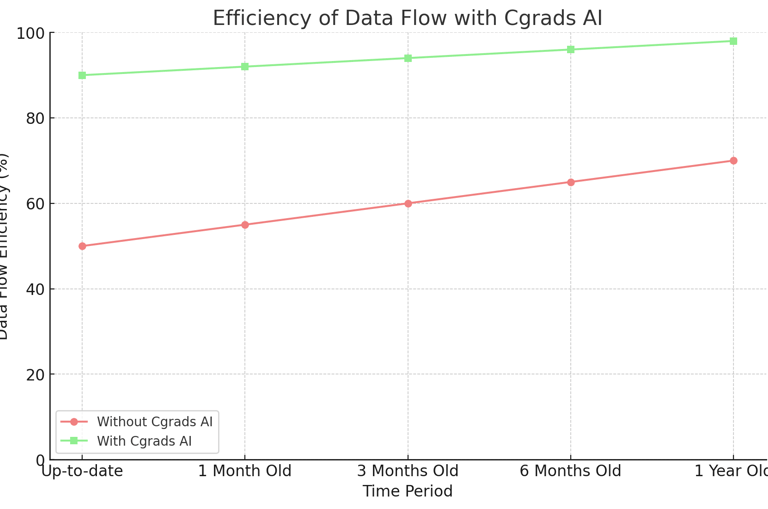
High Dimensional Data

Efficiently handling and retrieving high-dimensional data
Challenges:-
Scalability: Current vector databases struggle to maintain performance as the dataset size increases, especially beyond millions of vectors.
Performance: HNSW-based systems experience a notable drop in search accuracy and speed with increasing dataset sizes.
Cost-Efficiency: Maintaining high performance with HNSW requires substantial computational resources, leading to increased operational costs.
New Trends and Techniques
1. Emergence of ANN Index Algorithm
The Approximate Nearest Neighbor (ANN) index algorithm has emerged from academic research, presenting a promising alternative to HNSW. This algorithm focuses on balancing search accuracy with computational efficiency, making it suitable for both mid-sized and large-scale vector searches.
2. Intra-Query Parallel Graph Traversal
A key innovation in the ANN index algorithm is the use of intra-query parallel graph traversal technology. This technique allows for multiple graph traversal operations to be executed simultaneously within a single query, significantly improving search performance.
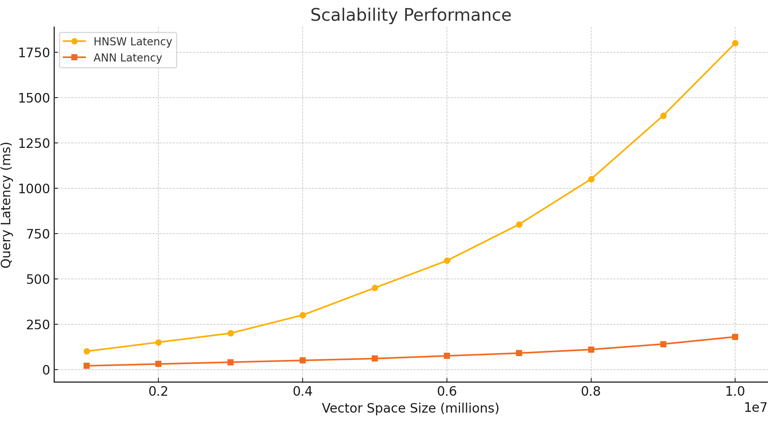
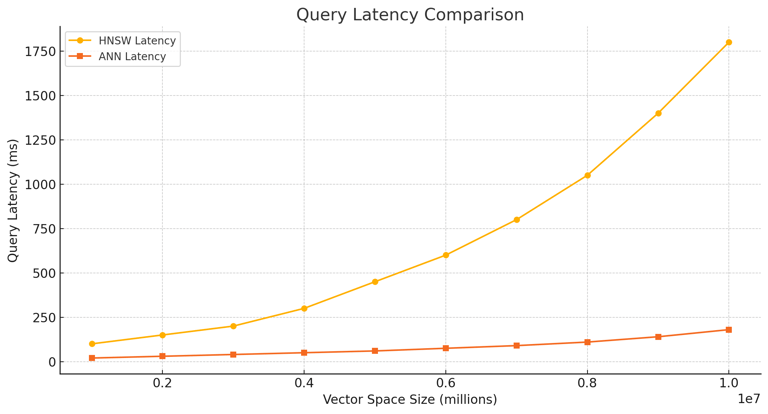
Graph 1: Query Latency Comparison :
This graph compares the query latency of HNSW and the new ANN index algorithm across different vector space sizes. Explanation: The ANN index algorithm consistently demonstrates lower latency compared to HNSW, with a more pronounced difference in larger vector spaces.
Scalability Analysis:
Graph 2: Scalability Performance:This graph illustrates the performance of both algorithms as the number of vectors increases from 1M to 10M. Explanation: The ANN index algorithm maintains stable performance across increasing dataset sizes, whereas HNSW shows a decline in efficiency.
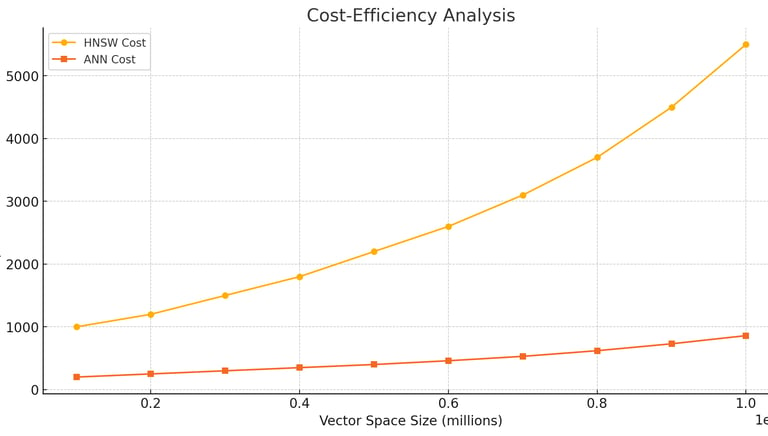
Cost-Efficiency :
Graph 3: Cost-Efficiency Analysis:This graph compares the computational cost required to achieve high search accuracy using HNSW and the ANN index algorithm.Explanation: The ANN index algorithm achieves high search accuracy with significantly lower computational costs compared to HNSW.
Solution: To address the challenges associated with HNSW in high-performance vector databases, a new vector search approach was developed from scratch, emphasizing scalability, performance, and cost-efficiency. This approach leverages the ANN index algorithm, which utilizes intra-query parallel graph traversal, resulting in substantial performance improvements.

DATA GOVERNANCE

Challenges:
Data Security: Identifying and protecting sensitive information, such as Personally Identifiable Information (PII) and proprietary data, is paramount to prevent data breaches and maintain user trust.
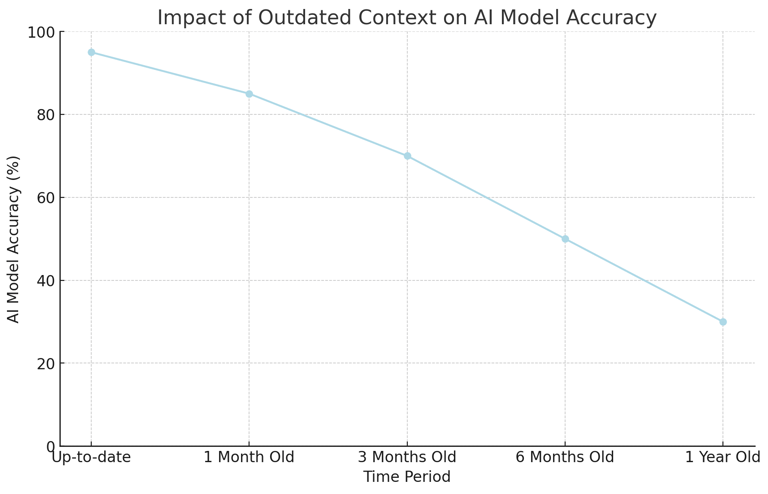
Data Relevance: Ensuring that the data used is relevant to the specific problem the LLM model is addressing to enhance model accuracy and performance.
Data Quality: Detecting and correcting inconsistencies and outdated information to avoid skewing the model's results and decisions.
Latest Trends and Techniques
1. Automated Data Compliance
Automated systems for verifying data compliance have become increasingly sophisticated. These systems use advanced algorithms to detect PII and proprietary data, ensuring that sensitive information is flagged and handled appropriately before it reaches the LLM models.
2. Data Relevance Analysis
Techniques for analyzing data relevance have advanced, leveraging machine learning to assess how closely data aligns with the specific problem the model is intended to solve. This ensures that only the most pertinent data is used, improving the model's efficiency and outcomes.
3. Inconsistency Detection
Machine learning algorithms are now capable of identifying and correcting inconsistencies within datasets. By flagging and resolving discrepancies, these systems help maintain high data quality, which is crucial for reliable model performance.
Solution:
Cgrads provides a comprehensive solution by offering automatic checks that ensure data compliance and quality. These checks include:
Verification of PII and Proprietary Data: Automatically detecting and managing sensitive information to prevent unauthorized access and use.
Data Relevance Assessment: Evaluating data to ensure it is pertinent to the specific problem the LLM model is addressing.
Inconsistency Detection: Identifying and rectifying inconsistencies to maintain data quality and prevent skewed model outcomes.
Key Benefits
Enhanced Data Security: Protects sensitive information, reducing the risk of data breaches and ensuring compliance with regulations.
Improved Model Accuracy: Ensures that only relevant data is used, enhancing the model's performance.
High Data Quality: Maintains the integrity of data, leading to more reliable and accurate model results.
Data Security
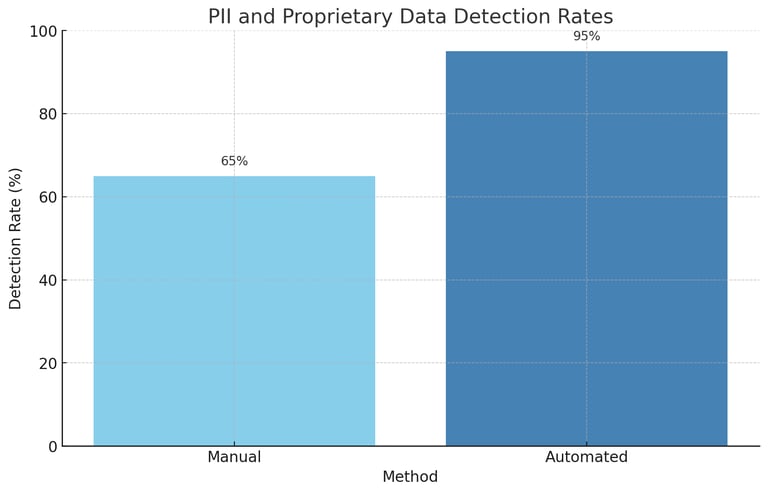
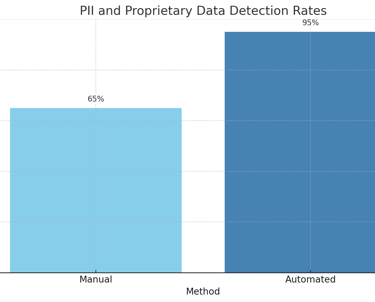
Chart 1: PII and Proprietary Data Detection Rates:
This chart shows the effectiveness of Cgrads automated checks in detecting PII and proprietary data compared to manual methods.Explanation: Automated checks significantly outperform manual methods in detecting sensitive information, ensuring better data security.
Data Relevance
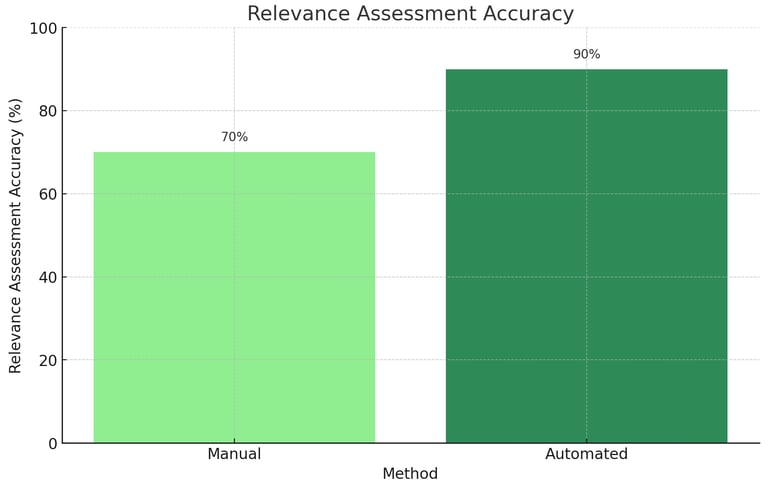
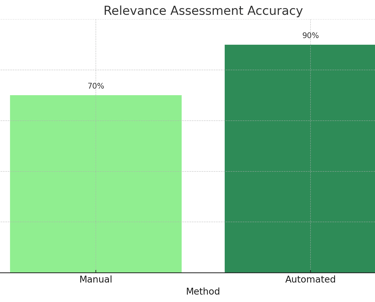
Chart 2: Relevance Assessment Accuracy
This chart compares the accuracy of data relevance assessment using traditional methods versus Cgrads automated relevance analysis.Explanation: Cgrads automated analysis consistently provides higher accuracy in assessing data relevance.
Data Quality
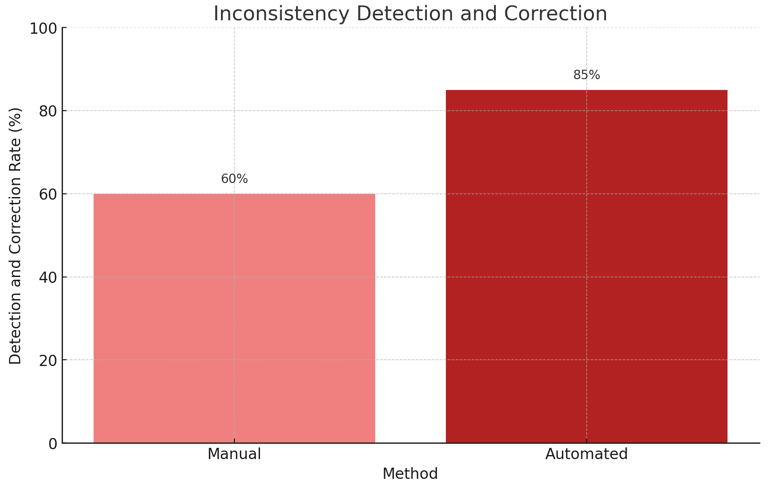
Chart 3: Inconsistency Detection and Correction
This chart illustrates the effectiveness of Cgrads in detecting and correcting data inconsistencies compared to traditional methods.Explanation: Automated systems detect and correct inconsistencies more effectively, ensuring higher data quality.
1. PII and Proprietary Data Detection Rates
This chart shows that automated methods significantly outperform manual methods in detecting sensitive information, with a detection rate of 95% compared to 65%.
2. Relevance Assessment Accuracy
This chart illustrates that automated relevance assessment provides higher accuracy, reaching 90%, compared to 70% for manual methods.
3. Inconsistency Detection and Correction
This chart demonstrates that automated systems detect and correct inconsistencies more effectively, with an 85% success rate, compared to 60% for manual methods.
Challenges
High Operational Costs: Outsourcing AML investigations is expensive, requiring substantial financial resources to manage and coordinate external analysts.
Inefficient Use of Time: AML investigators spend a majority of their time on non-investigative tasks, reducing their efficiency and productivity.
Backlogs and Compliance Risks: Delays in processing AML alerts can result in growing backlogs, increasing the risk of non-compliance and potential fines.
Latest Trends and Techniques
1. AI-Driven Automation
The integration of Artificial Intelligence (AI) agents in AML processes is a growing trend. AI agents, equipped with Large Language Models (LLMs), can automate routine tasks, reducing the workload on human investigators.
2. Multi-Source Data Integration
Modern AI systems leverage over 200 data sources to analyze and act on false positives, investigate high-risk clients, and create audit-ready narratives. This multi-source integration ensures comprehensive and accurate analysis.
3. Real-Time Monitoring and Escalation
AI agents operate 24/7, continuously monitoring for suspicious activities. They can escalate cases to full-time employees for further investigation, ensuring that critical decisions remain under human control.
Solution
Cgrad's AI Agents provide a comprehensive solution by learning the alert review process and working continuously to handle basic Know Your Customer (KYC) and AML tasks. Here’s how it works:
Choose where you need to supplement your staff: Identify the areas within your compliance operations that require additional support.
Add your policy, data sources, and inaccuracy thresholds: Customize the AI agents to align with your specific policies and data sources, and set thresholds for acceptable inaccuracies.
Review escalated cases: Focus on high-risk and escalated cases that require human judgment and decision-making.
Schedule a demo: See firsthand how Cgrad's AI agents can enhance your compliance operations.
Key Benefits
Higher Quality and Transparency: AI agents provide consistent and transparent reviews, ensuring higher quality in AML processes.
Significant Cost Savings: Automated systems reduce the need for expensive human reviewers, leading to significant cost savings.
Scalable Compliance Operations: Near-instant compliance capacity allows your team to focus on high-priority initiatives, unlocking growth opportunities.
Operational Efficiency
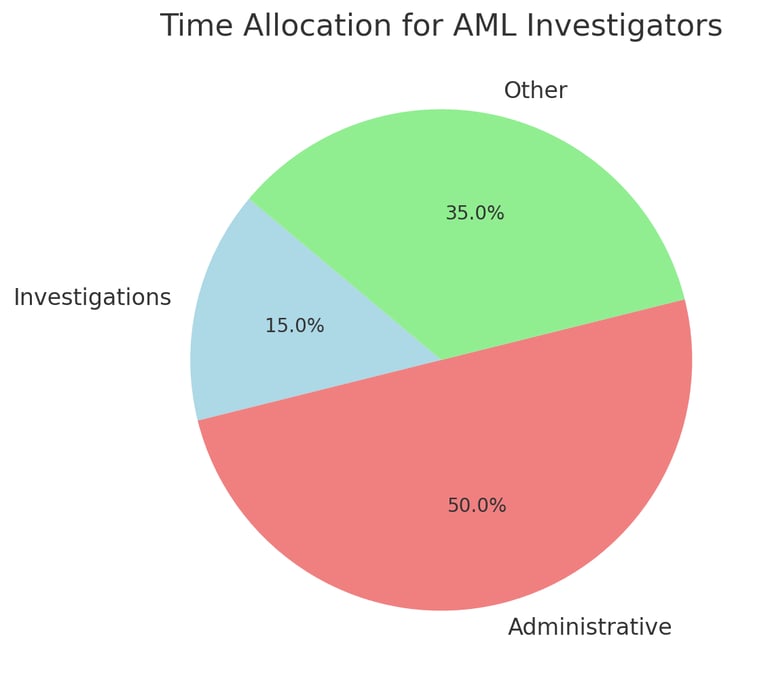
Chart 1: Time Allocation for AML Investigators
This chart illustrates the percentage of time spent on various tasks by AML investigators, highlighting the inefficiencies in the current system.Explanation: AML investigators spend only 15% of their time on actual investigations, with the remaining time consumed by administrative and non-investigative tasks.
Cost Comparison
Chart 2: Cost Comparison of Human vs. AI-Driven AML Investigations
This chart compares the operational costs of traditional human-based AML investigations with AI-driven approaches.Explanation: AI-driven approaches significantly reduce costs compared to traditional human-based methods.
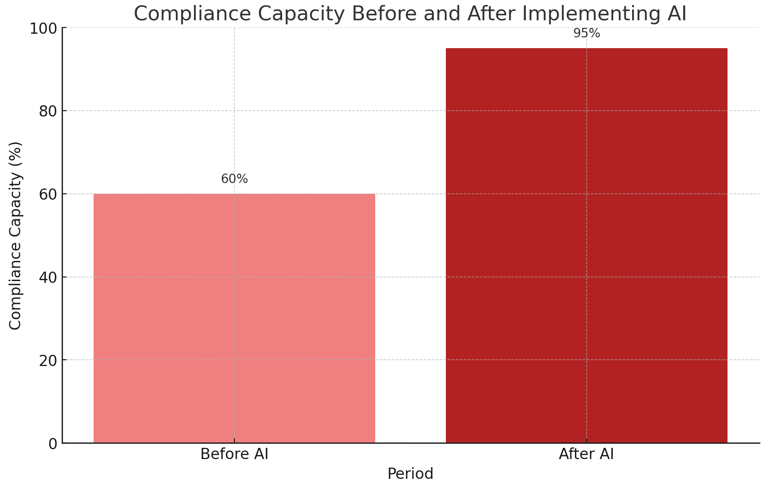
Compliance Capacity
Chart 3: Compliance Capacity Before and After Implementing AI
This chart shows the compliance capacity of a fintech company before and after implementing Cgrad's AI agents.Explanation: Implementing AI agents leads to a dramatic increase in compliance capacity, allowing for more efficient handling of AML tasks.



Challenges
Complexity and Volume of Threats: Security design reviews must consider numerous potential threats, making it easy to miss critical risk areas.
Inefficient Collaboration: Meetings between security and engineering teams are often messy and time-consuming.
Understaffed Security Teams: A high security-to-engineering staff ratio results in insufficient resources for thorough reviews, causing delays in the development process.
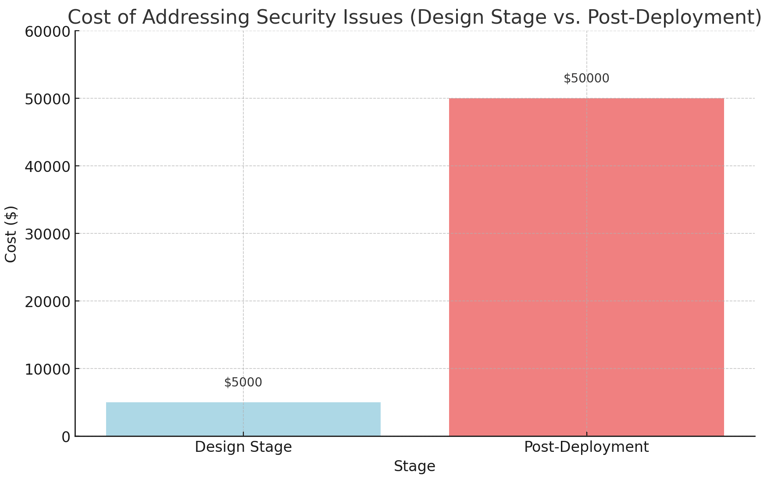
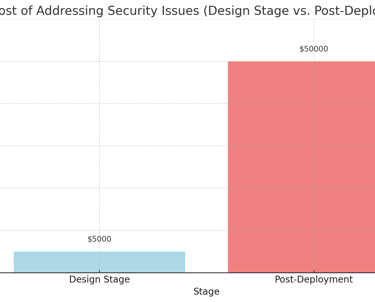
High Cost of Post-Deployment Fixes: Security breaches are significantly more costly to address after deployment than identifying and mitigating risks during the design stage.
Latest Trends and Techniques
1. Leveraging Large Language Models (LLMs)
LLMs, such as GPT-4, can automate initial security design inspections by analyzing designs and identifying potential risks. These models provide detailed insights and generate relevant questions and comments for further review.
2. Automated Security Design Reviews
Automated systems can identify which security designs need review, perform initial inspections using LLMs, and present findings to security teams for final decision-making. This streamlines the review process and reduces the burden on security teams.
3. Risk-Based Prioritization
Tools that help engineers view a prioritized list of pending security designs based on risk levels ensure that the most critical issues are addressed first, optimizing resource allocation.
4. Detailed, Insightful Feedback
LLMs generate comprehensive questions and comments focused on specific risks, enhancing the depth and quality of security reviews.
SOLUTIONS: Cgrads' Automated Security Review System leverages LLMs to streamline and enhance the security design review process, making it more efficient, accurate, and cost-effective.
Key Features
Initial Inspections by LLMs: LLMs conduct initial inspections of security designs, identifying potential risks and generating detailed questions and comments.
Automated Assessment Presentation: The system presents its findings to security team members, who make the final decisions on the questions or comments to include.
Risk-Based Prioritization: Engineers can view a prioritized list of security designs pending review, along with their risk levels, ensuring that the most critical issues are addressed promptly.
Comprehensive Insights: LLMs provide detailed insights focused on specific risks, improving the quality and depth of reviews.
Implementation Process
Identify Security Designs: The system identifies which security designs require review.
Initial Inspection by LLMs: LLMs conduct initial inspections and generate questions and comments.
Review by Security Team: Security team members review the assessments and make final decisions.
Engineer Prioritization: Engineers prioritize reviews based on risk levels and address the most relevant issues.
Key Benefits
Efficiency: Automates initial inspections, reducing the time and resources required for security design reviews.
Improved Accuracy: Enhances the accuracy of reviews with detailed insights from LLMs.
Cost Savings: Identifies risks early in the design stage, reducing the high costs of post-deployment fixes.
Better Collaboration: Reduces the need for extensive meetings between security and engineering teams.
Optimized Resources: Helps understaffed security teams prioritize and address high-risk issues effectively.
Cost Comparison
Chart 1: Cost of Addressing Security Issues (Design Stage vs. Post-Deployment)
This chart compares the cost of addressing security issues during the design stage versus post-deployment.Explanation: Addressing security issues during the design stage is significantly more cost-effective than dealing with breaches post-deployment.
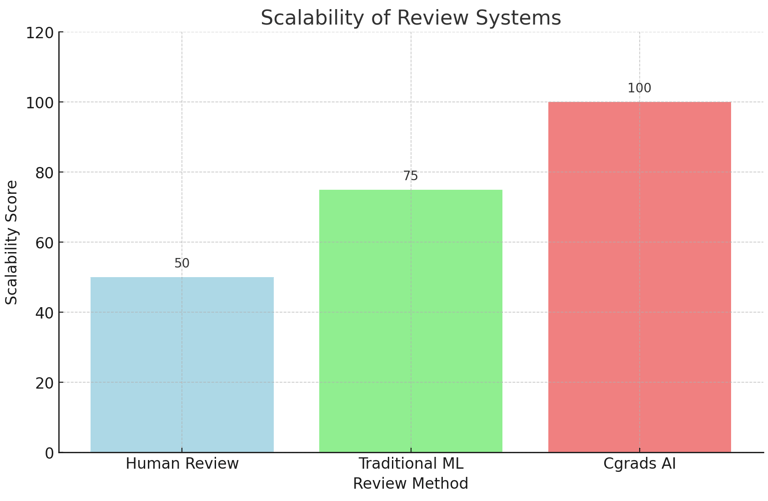
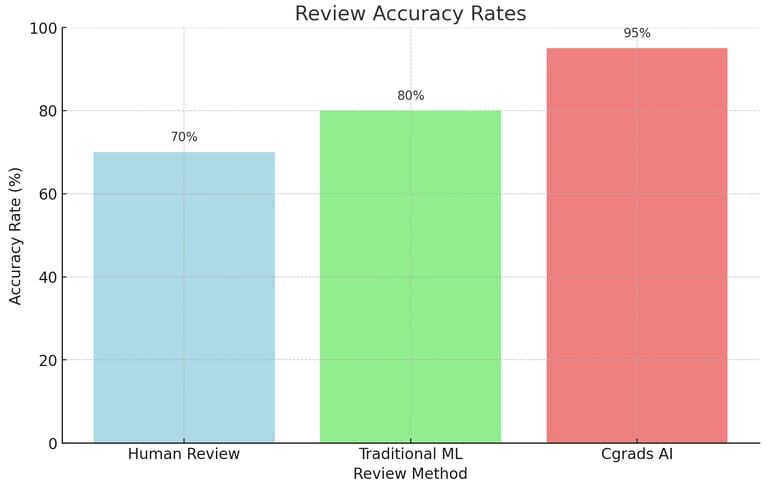
Review Accuracy
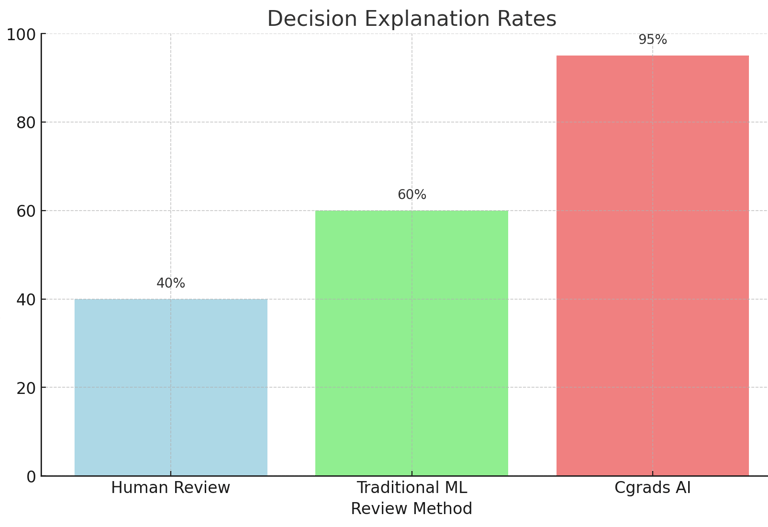
Chart 2: Review Accuracy Rates
This chart illustrates the accuracy rates of traditional human reviews, traditional ML systems, and Cgrads' automated system.Explanation: Cgrads' system demonstrates higher accuracy rates than human and traditional ML reviews.
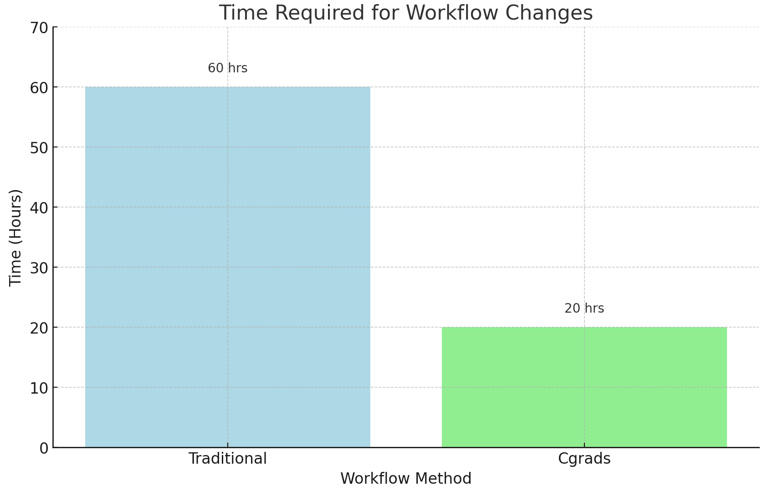
Efficiency of Workflow Changes
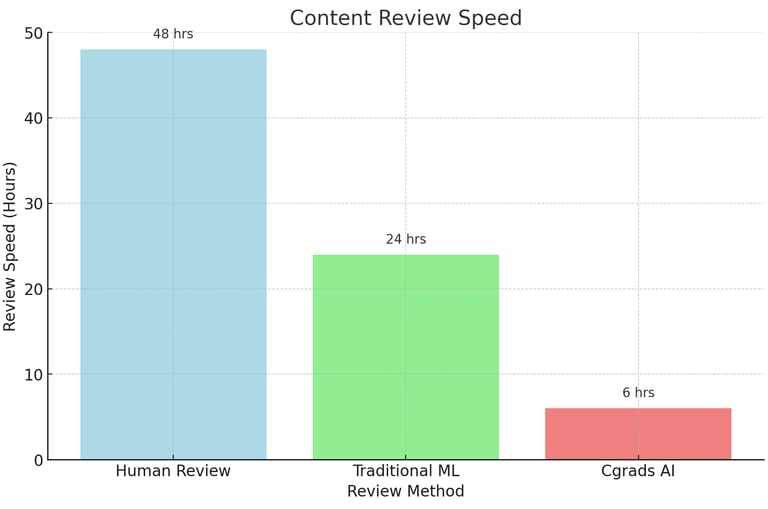
Chart 3: Time Required for Workflow Changes
This chart shows the time required to implement workflow changes in traditional systems versus Cgrads' automated system.Explanation: Cgrads' system implements workflow changes more quickly than traditional methods.
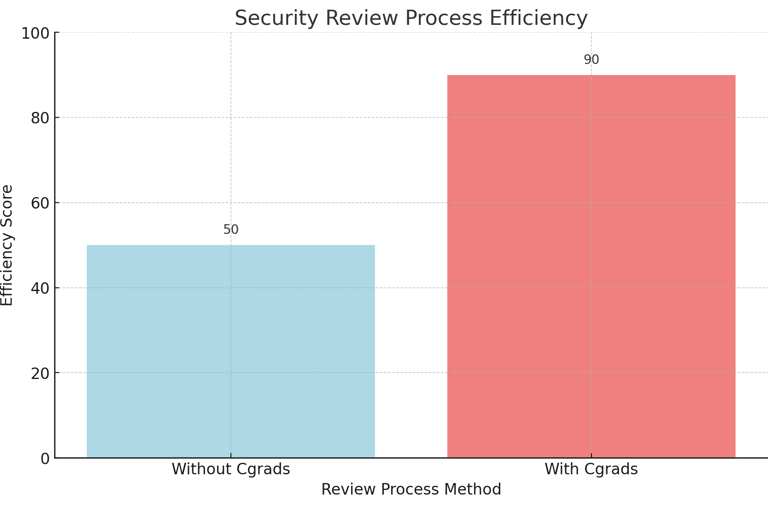
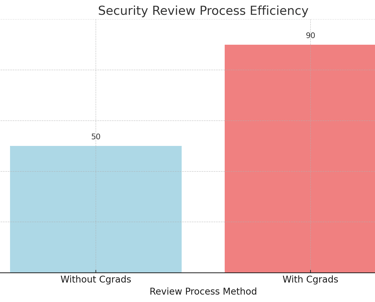
Security Review Process
Chart 4: Security Review Process Efficiency
This chart compares the efficiency of the security review process with and without Cgrads' automated system.Explanation: Cgrads' system streamlines the security review process, improving efficiency and reducing delays.