AI Projects
Challenges:-
Complexity and Volume of Threats: Security design reviews must consider numerous potential threats, making it easy to miss critical risk areas.
Inefficient Collaboration: Meetings between security and engineering teams are often messy and time-consuming.
Understaffed Security Teams: A high security-to-engineering staff ratio results in insufficient resources for thorough reviews, causing delays in the development process.
High Cost of Post-Deployment Fixes: Security breaches are significantly more costly to address after deployment than identifying and mitigating risks during the design stage.
Latest Trends and Techniques
1. Leveraging Large Language Models (LLMs)
LLMs, such as GPT-4, can automate initial security design inspections by analyzing designs and identifying potential risks. These models provide detailed insights and generate relevant questions and comments for further review.
2. Automated Security Design Reviews
Automated systems can identify which security designs need review, perform initial inspections using LLMs, and present findings to security teams for final decision-making. This streamlines the review process and reduces the burden on security teams.
3. Risk-Based Prioritization
Tools that help engineers view a prioritized list of pending security designs based on risk levels ensure that the most critical issues are addressed first, optimizing resource allocation.
4. Detailed, Insightful Feedback
LLMs generate comprehensive questions and comments focused on specific risks, enhancing the depth and quality of security reviews.
SOLUTIONS:-
Cgrads' Automated Security Review System leverages LLMs to streamline and enhance the security design review process, making it more efficient, accurate, and cost-effective.
Key Features
Initial Inspections by LLMs: LLMs conduct initial inspections of security designs, identifying potential risks and generating detailed questions and comments.
Automated Assessment Presentation: The system presents its findings to security team members, who make the final decisions on the questions or comments to include.
Risk-Based Prioritization: Engineers can view a prioritized list of security designs pending review, along with their risk levels, ensuring that the most critical issues are addressed promptly.
Comprehensive Insights: LLMs provide detailed insights focused on specific risks, improving the quality and depth of reviews.
Implementation Process
Identify Security Designs: The system identifies which security designs require review.
Initial Inspection by LLMs: LLMs conduct initial inspections and generate questions and comments.
Review by Security Team: Security team members review the assessments and make final decisions.
Engineer Prioritization: Engineers prioritize reviews based on risk levels and address the most relevant issues.
Key Benefits
Efficiency: Automates initial inspections, reducing the time and resources required for security design reviews.
Improved Accuracy: Enhances the accuracy of reviews with detailed insights from LLMs.
Cost Savings: Identifies risks early in the design stage, reducing the high costs of post-deployment fixes.
Better Collaboration: Reduces the need for extensive meetings between security and engineering teams.
Optimized Resources: Helps understaffed security teams prioritize and address high-risk issues effectively.
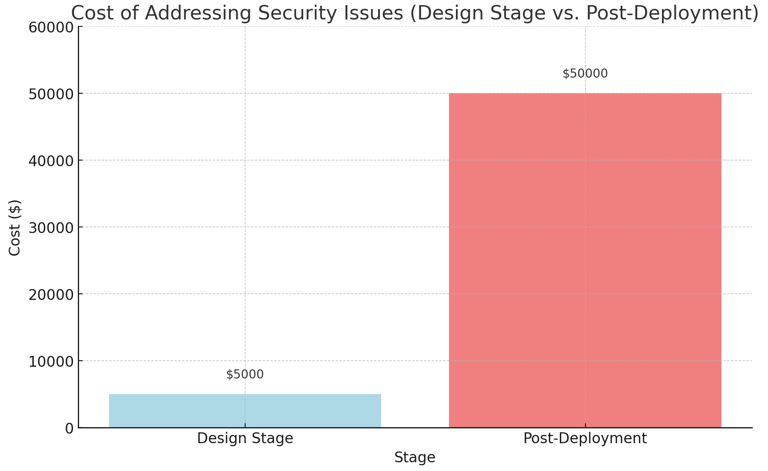
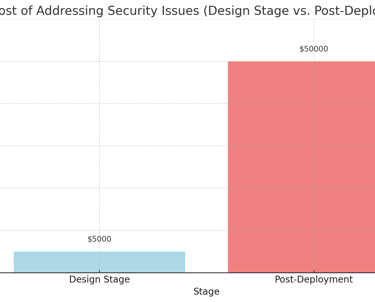
Cost Comparison:
Chart 1: Cost of Addressing Security Issues (Design Stage vs. Post-Deployment)
This chart compares the cost of addressing security issues during the design stage versus post-deployment.Explanation: Addressing security issues during the design stage is significantly more cost-effective than dealing with breaches post-deployment.
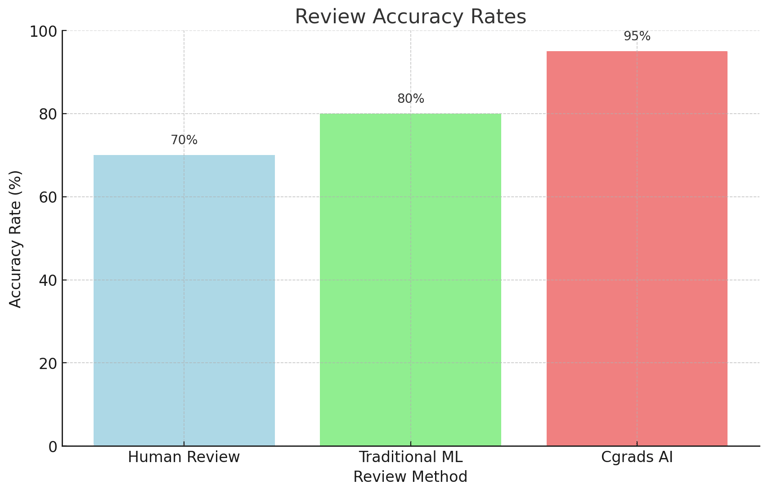
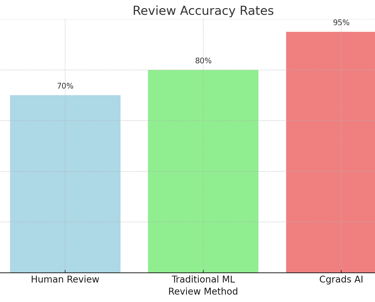
Review Accuracy
Chart 2: Review Accuracy Rates
This chart illustrates the accuracy rates of traditional human reviews, traditional ML systems, and Cgrads' automated system.Explanation: Cgrads' system demonstrates higher accuracy rates than human and traditional ML reviews.
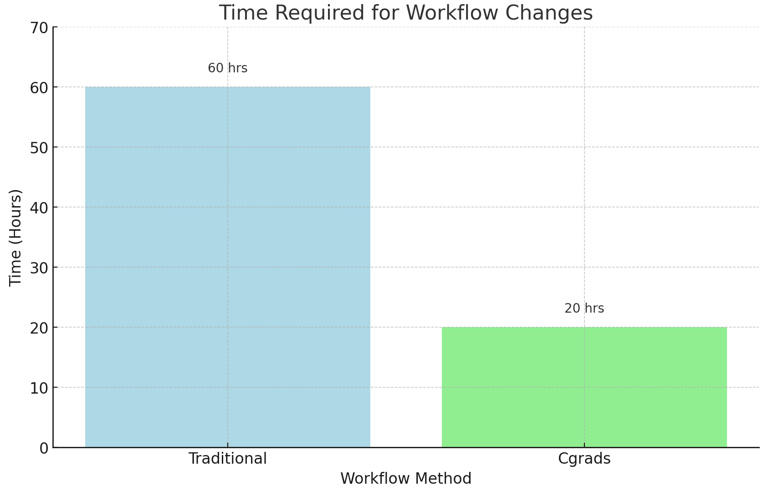
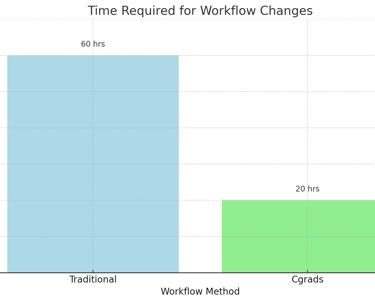
Efficiency of Workflow Changes
Chart 3: Time Required for Workflow Changes
This chart shows the time required to implement workflow changes in traditional systems versus Cgrads' automated system.Explanation: Cgrads' system implements workflow changes more quickly than traditional methods.
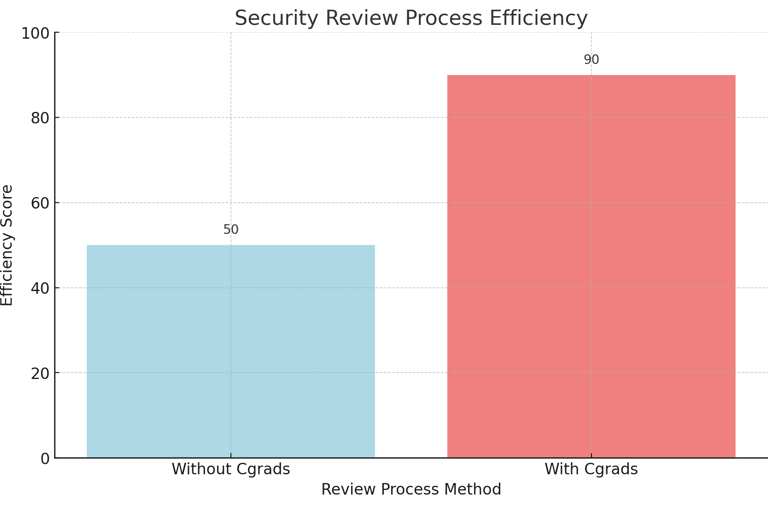
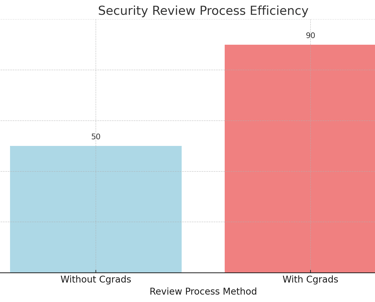
Security Review Process
Chart 4: Security Review Process Efficiency
This chart compares the efficiency of the security review process with and without Cgrads' automated system.Explanation: Cgrads' system streamlines the security review process, improving efficiency and reducing delays.